14 Apr April 2023 – MacAdmins Meeting
April 19, 2023 – University of Utah, MacAdmins Meeting

The University of Utah, MacAdmins Meeting is held monthly virtually on the 3rd Wednesday of each month at 11 AM Mountain Time. Presentations cover Apple technology and integration in a heterogeneous university enterprise environment. This month’s meeting will be held on Wed, April 19th, 2023 at 11 AM MT and we will provide live broadcasts and archives that will be made available 2-3 days after the meeting.
Microsoft Defender for Endpoint on macOS Best Practices – Yong Rhee, Microsoft Product Manager for Microsoft Defender
This presentation will cover Microsoft Defender for Endpoint on macOS, best practices, and FAQs by Microsoft Product Manager for Microsoft Defender for Endpoint.
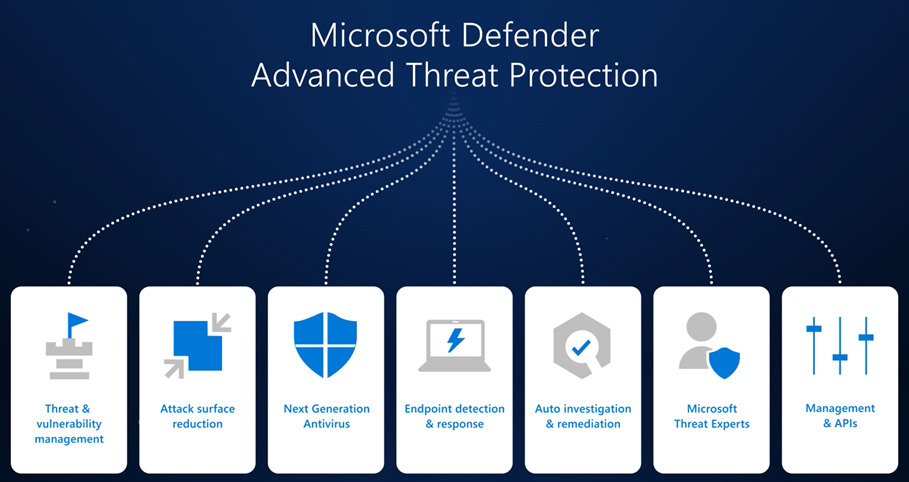
Microsoft Defender for Endpoint on macOS is a security solution provided by Microsoft to protect macOS devices against various cyber threats. It is designed to provide advanced threat protection and endpoint detection and response (EDR) capabilities to macOS devices, such as MacBooks and iMacs, which are commonly used in enterprise environments. It includes features such as real-time protection against viruses, malware, and other malicious software, as well as advanced threat detection and response capabilities such as automated investigation and remediation of security incidents.
Here are some best practices for using Microsoft Defender for Endpoint on macOS:
- Keep the application up to date: Ensure that you keep the Microsoft Defender for Endpoint application up to date with the latest security updates to ensure maximum protection against new threats.
- Enable real-time protection: Enable real-time protection to ensure that the system is being monitored for any suspicious activity or malware at all times.
- Perform regular scans: Schedule regular scans of your system to check for any potential threats that may have slipped through the real-time protection.
- Use recommended exclusions: Microsoft recommends specific exclusions for files, folders, and processes that should be excluded from scanning to avoid performance issues.
- Utilize quarantine and removal features: If any malware is detected, use the quarantine and removal features of Microsoft Defender for Endpoint to isolate and remove the threat.
- Educate users: Educate users on how to recognize and report suspicious activity, and encourage them to avoid downloading and installing untrusted software.
About Yong Rhee
Yong Rhee is a Product Manager for Microsoft Defender for Endpoint, and the areas that he owns are the macOS experience and 1st party Datacenter. He has been with Microsoft in different roles such as Customer Experience Engineering (CxE), Premier Field Engineering (PFE, consulting), and CSS.
- Video – To view the archived presentation video, click here.
- Slides – To view the archived presentation slides, click here.
Octory Overview – Guillermo Leal Llano & Benjamin Richard
Octory is a highly customizable and fully integrated macOS application to onboard, guide, and support your users through an outstanding experience. With Octory, IT admins can streamline the setup process, track and automate software installations and configurations, and create a personalized experience. During the overview, we will demonstrate a couple of use cases currently used by our customers and explain where to start. 
Octory’s interface is made up of three main blocks: Slides, Containers, and Components. Slides are like slides in presentation software and hold containers stacked horizontally, while containers hold components vertically. Components have fixed or adaptive heights and take up available space in containers. The application uses a configuration file to adapt its interface and behavior. It also uses a privileged Helper to execute commands with root privileges securely. Octory retrieves system and hardware information for internal use and sends requests to an API if specified in the configuration, securely storing API credentials in the keychain. The application can read any folder readable by the end-user, and log files can be accessed at /tmp/[username]-octory.log. Octory comes in three different options for deployment. The main package is recommended as it installs all necessary files in the Mac system. A blank configuration file is included and can be customized, or presets can be used from the Presets folder. The configuration file should be placed in the System’s Library /Library/Application Support/Octory/Octory.plist with the correct permissions. The application can be launched using the command line or by opening Octory application. A custom configuration file can be launched using the -c or –config option, and the default configuration file can be changed using the –save flag.
About Guillermo Leal Llano – Apple Lead Consultant
Guillermo is an Apple Distinguished Educator, Jamf trainer, and seasoned professional with more than 15 years of experience. He serves as an advisor and expert for IT deployments related to Apple technologies in Education and Enterprise.
About Benjamin Richard – Head of Modern Device Management
Benjamin is a skilled IT professional with 10+ years of experience in telecom, networking, and device management. He has managed complex global projects, showcasing expertise with Windows, Android, and Apple devices. He manages the modern device management practice at Amaris Consulting.
- Video – To view the archived presentation video, click here.
- Slides – To view the archived presentation slides, click here.
AI for MacAdmins – James Reynolds, University of Utah
Computers only understand numbers. Unicode is letters mapped to numbers. JPEGs are images mapped to numbers. MP3s are sounds mapped to numbers. Siri, Alexa, and similar voice assistants are words mapped to numbers. Large language models are meanings mapped to numbers. 
In this presentation, James will explain this and other AI important concepts and shows several AI products, including ChatGPT, GitHub Copilot, several AI command line tools, the AI built into the current iTerm beta, and the OpenAI and LangChain Python AI libraries. He’ll also show how easy it is to run Stable Diffusion and LLaMA on an Apple Silicon Mac.
For MacAdmins, ChatGPT can be a valuable tool for obtaining quick and accurate information about macOS management and troubleshooting. It can help MacAdmins save time and effort by providing useful tips, instructions, and solutions to common problems related to macOS deployment, configuration, and maintenance. ChatGPT can also assist MacAdmins in automating tasks, creating scripts, and implementing workflows that can increase productivity and efficiency.
GitHub Copilot is an AI-powered code autocompletion tool developed by GitHub and OpenAI. It is designed to help developers write code more efficiently and accurately by suggesting code snippets and completing code as they type. The tool works by analyzing the code context and generating suggestions based on the patterns it detects. It can also learn from the user’s code as they work, improving its suggestions over time.
The iTerm beta has introduced an artificial intelligence feature that allows users to leverage machine learning to assist in their command-line tasks. This feature uses OpenAI’s GPT-3 language model to provide auto-completion suggestions and command-line argument predictions in real time as users type their commands. Users can adjust the AI model used by changing the “OpenAI Model name” advanced setting. It is important to note that this feature is not free and requires an OpenAI API key to use.
- Video – To view the archived presentation video, click here.
- Slides – To view the archived presentation slides, click here.
Open Discussion
Questions, comments, problems, and fixes.
Directions
Due to the coronavirus (aka Covid-19) crisis, this meeting will not be meeting in person but will currently be done virtually using Zoom video communications architecture.
- Require a Password to Join This meeting will require a password to join the meeting. Information will be emailed via a campus internal list, but if you are external and want to attend the meeting, please use the contact us form to receive details. Else, the archive of the meeting will be available 2-3 days after the live meeting.

- Miscellaneous We will also implement other settings and safeguards to secure the meeting.
Archived Presentation(s)
- Archives of the presentations will be available on this web page.


No Comments